TL;DR:
It is not necessary to update that certificate.
Comment about that situation:
Those files were timestamped and will be valid after the cert expires. In case of UEM the certs were internal and have no timestamp service, that's why it was such a mess.
https://knowledge.digicert.com/generalinformation/INFO1119.html
“Is timestamped code valid after a Code Signing Certificate expires?
Digicert timestamp services allow you to timestamp your signed code. Timestamping ensures that code will not expire when the certificate expires because the system validates the timestamp. If you use the timestamping service when signing code, a hash of your code is sent to the timestamp server to record a timestamp for your code. A user’s software can distinguish between code signed with an expired certificate that should not be trusted and code that was signed with a certificate that was valid at the time the code was signed but which has subsequently expired.
Please specify the timestamp server URL you need when you sign your code. Digicert provides you with both an SHA-1 and SHA-256 RFC 3161 timestamping URLs.
The timestamp server validates the date and the time that the file was signed therefore the certificate can expire, but the signature will be valid for as long as the file is in production. A new certificate is only necessary if you want to sign an additional code or re-sign a code that has been modified.
If you do not use the timestamping option during the signing, you must re-sign your code and re-send it out to your customers.
To verify if your file has been timestamped, you can use the verifying commands provided in our knowledge base articles. The date and time will be displayed when the file has been timestamped. No dates or a warning will appear when the file has NOT been timestamped.
See: Instructions to sign and timestamp your code.” (edited)
Also, info from VMware communities forum :
As per our discussion, the internal certificates responsible for these DLLs would be expected to regenerate once they expire tomorrow morning. No action is required until this time, where you can check to see that they were recreated successfully.
After checking internally, this will not be a problem for horizon as it is not sign in the same way.
UEM was using an internal CA for some services without timestamps now corrected but horizon uses a public CA with timestamps.
“Is timestamped code valid after a Code Signing Certificate expires?
Digicert timestamp services allow you to timestamp your signed code. Timestamping ensures that code will not expire when the certificate expires because the system validates the timestamp. If you use the timestamping service when signing code, a hash of your code is sent to the timestamp server to record a timestamp for your code. A user’s software can distinguish between code signed with an expired certificate that should not be trusted and code that was signed with a Certificate that was valid at the time the code was signed but which has subsequently expired.
Please specify the timestamp server url you need when you sign your code. Digicert provides you with both a SHA-1 and SHA-256 RFC 3161 timestamping URLs.
The timestamp server validates the date and the time that the file was signed therefore the certificate can expire but the signature will be valid for as long as the file is in production. A new certificate is only necessary if you want to sign additional code or re-sign code that has been modified.
If you do not use the timestamping option during the signing, you must re-sign your code and re-send it out to your customers.
To verify if your file has been timestamped, you can use the verifying commands provided in our knowledge base articles. The date and time will be displayed when the file has been timestamped. No dates or a warning will appear when the file has NOT been timestamped.
See: Instructions to sign and timestamp your code.”
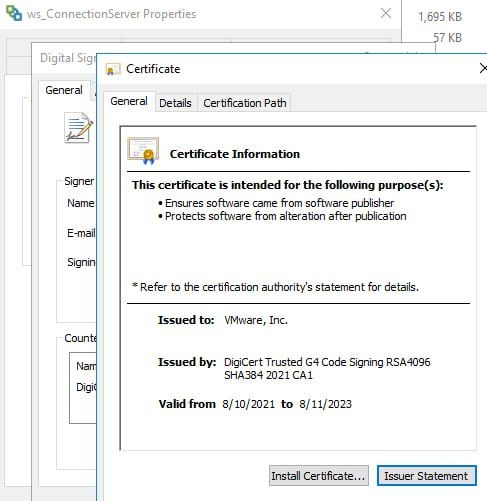
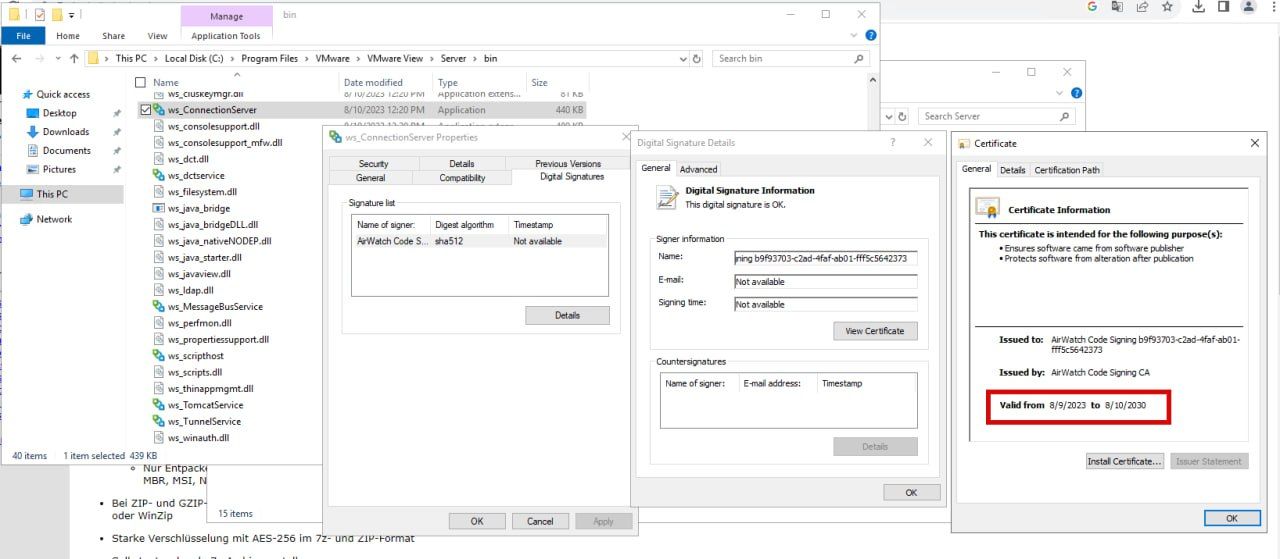
But, if you want to update certificate that is used for Digital Signing at Horizon env you can use Digital signing utility tool for AirWatch (new certs will be issued by AirWatch Code Signing CA).
Download this archive, extract it:
Before you start, you should stop all Horizon services!
Inside archive, you can find README file:
Steps for execution:
In a Powershell window running with Administrator privileges:
1. Navigate to the to directory where the tool exists:
> CD <current folder with this README>
2. Run script:
> .\SignUemDlls.ps1 "<full path to Horizon installtion folder root>"
e.g.
> .\SignUemDlls.ps1 "C:\Program Files\VMware\VMware View\Server"
Addition Information:
> The entire signing process may take up to 60 minutes to finish depending on the resources of the server.
> The text output of the Powershell window may appear to be frozen. This could be caused by the "QuickEdit Mode" mode being on for the Powershell window, which pauses the window's output when mouse is clicked inside the window. When you are in doubt about whether the process is actually stuck, mouse click inside the window and hit the enter key. It's safe to hit the enter key in the window.
> Watch the output screen looking for signing errors. The error count should be 0 for UEM services to start successfully. If the error count is not zero, run the same script again.
> The tool uses multiple processes for parallel processing. In rare cases, the tool may run into deadlock and the output screen will not progress for 10 minutes. In that case, stop the Powershell process and rerun the script.After finishing the procedure start all services or perform a reboot.
Comments?
Leave us your opinion.